RCE on Apache Struts 2.5.30 and 6.x
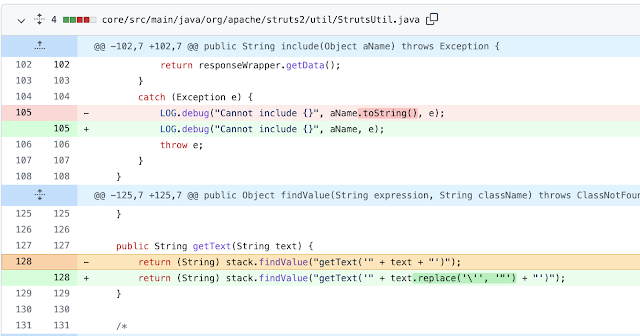
RCE in Apache Struts 2.5.30 and 6.x Abstract In early May 2021 I reported a second RCE on Apache Struts 2.5.0-2.5.29 here and disclosed the details a month after the fix was made public. Again, like many of you security researchers, I had to look more into it. So I kept digging and found a bypass to one of the RCE's that got fixed, which I'll briefly be describing here. There is no CVE identifier for this. To be clear, this is a rare situation that most programs wont run into and applies specifically to a 'select' type object. It is considered by Apache Struts to be a developer error in which the developer is forcing an evaluation ('%{}') with untrusted user input and thus not a vulnerability. Please see Apache Struts's Security page for more details on this. Vulnerability Analysis A reminder, OGNL evaluations are exploitable when OGNL code is evaluated twice. If you need an example of that please read through the previous two RCEs I wrote about. The b