Vulnerabilities In Apache Commons-Text 1.10.0

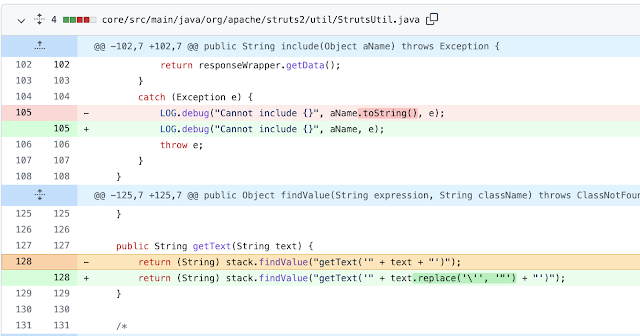
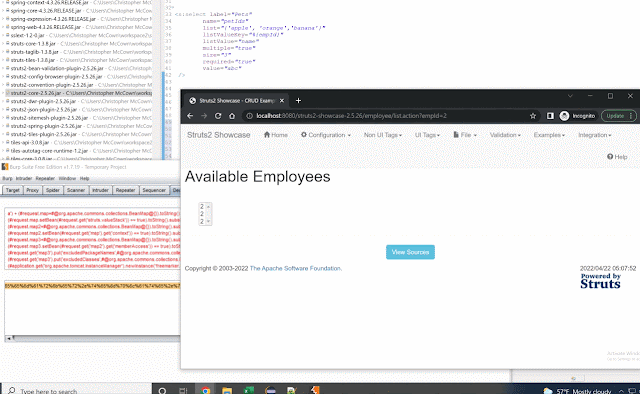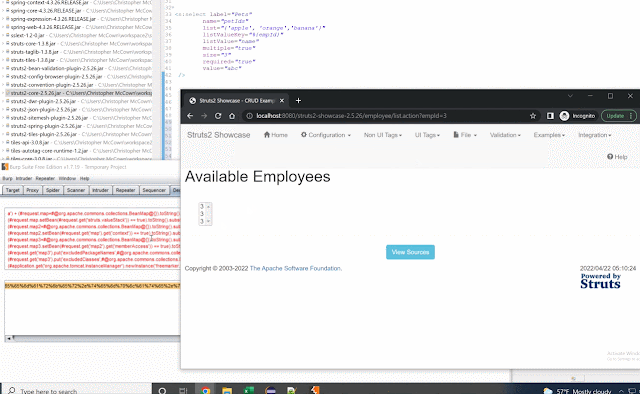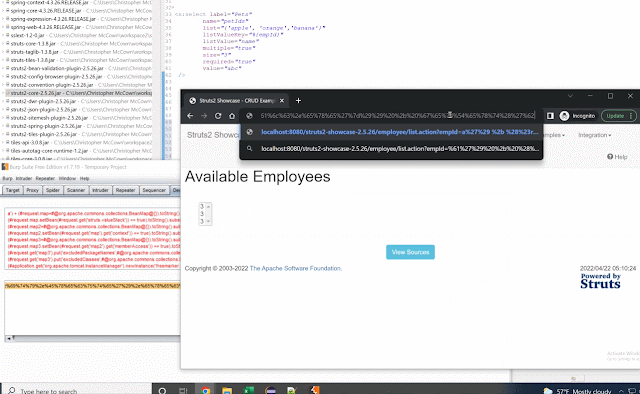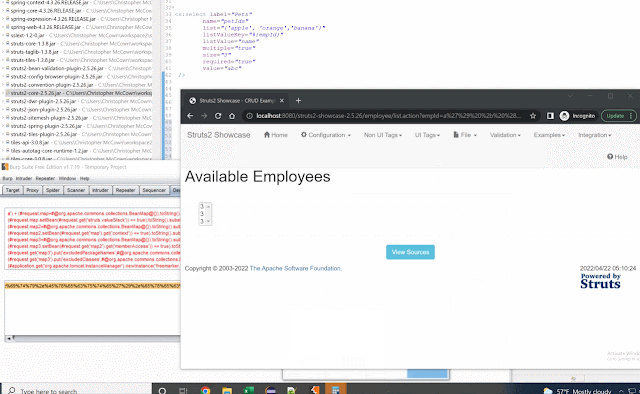
Vulnerabilities In Apache Commons-Text 1.10.0 Abstract In October 2022 a vulnerability in Apache Commons-Text was reported ( CVE-2022-42889 ) dubbed "Text4Shell". This vulnerability, while less prevalent, acted somewhat similar to log4shell which used interpolators to perform string lookups on user defined input that resulted in code execution. Like most software, there's often other related issue(s) found in neighboring code that don't get fixed when a big issue like this is reported. This blog is on those other vulnerabilities. Background CVE-2022-42889 "Text4Shell" was centered on an unsafe script evaluation found in the ScriptStringLookup. A POC looked like the following (seen at GHSL-2022-018 ): final StringSubstitutor interpolator = StringSubstitutor . createInterpolator (); String out = interpolator . replace ( "${script:javascript:java.lang.Runtime.getRuntime().exec('touch /tmp/foo')}" ); System . out . println ( out ...